I’ve developed many projects, and all the time, the decision was direct: let’s create a container with Docker.
But recently, I’ve reached some dead-ends with the containers, so I’d to made the question: VM or Container?
While containers have become the de-facto standard for modern applications, the lines between these two technologies are starting to blur. The rise of new, security-focused container runtimes proves that developers and infrastructure engineers are seeking a middle ground. Let’s break down the core differences and explore the tools that are changing the game.
The Core Difference: How They Handle Isolation
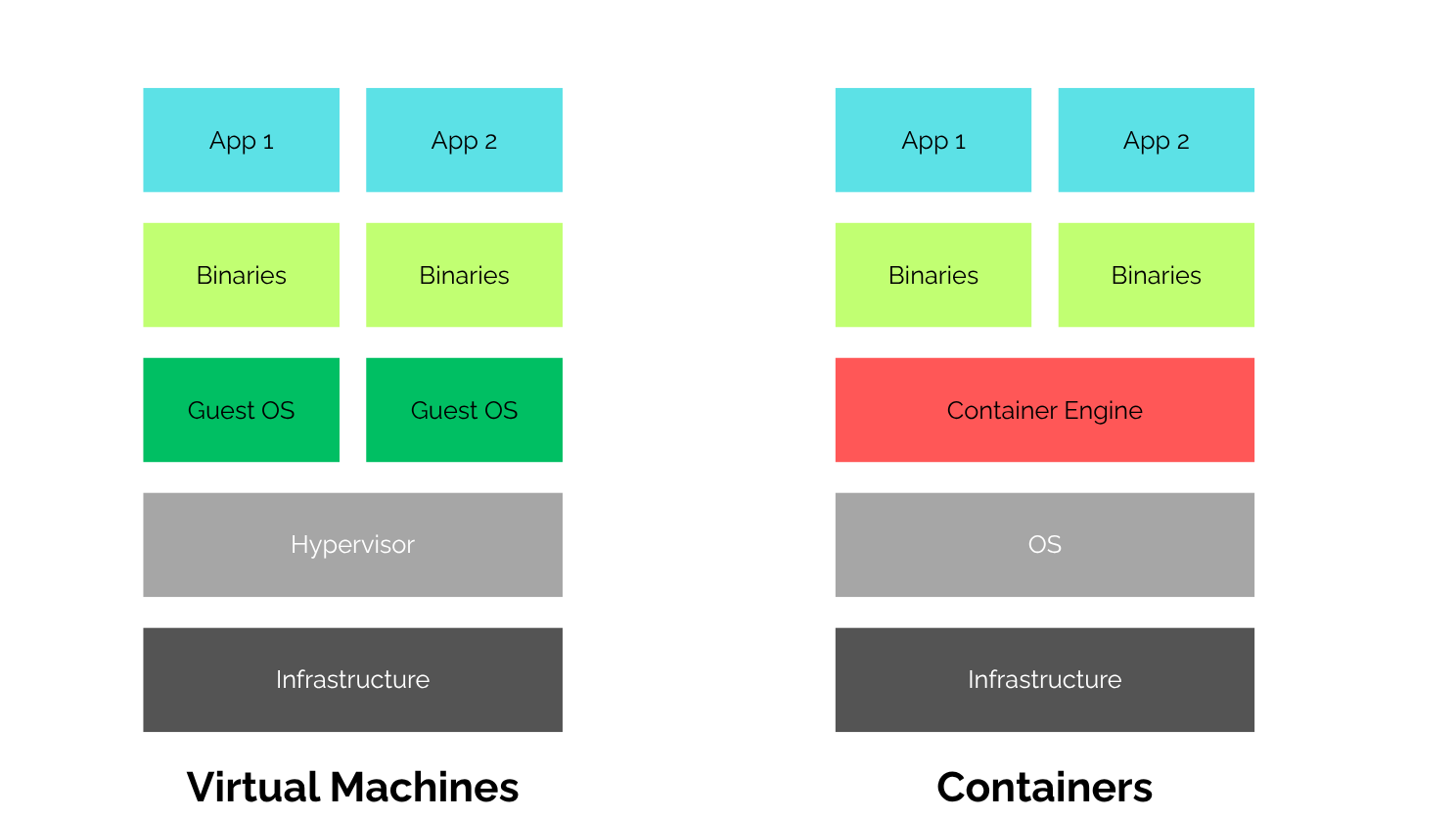
The fundamental distinction between a VM and a container lies in their isolation model.
- Virtual Machines achieve strong isolation by virtualizing the hardware. Each VM has its own guest operating system (OS), kernel, and virtualized hardware. This means the hypervisor is the only piece of software shared between VMs. Because of this architectural design, VMs are naturally more secure—a compromise in one VM doesn’t typically affect the host or other VMs. The downside is the overhead of running a full OS for every single application, making them slower to start and more resource-intensive.
- Containers, on the other hand, share the host OS kernel. They achieve isolation at the process level using technologies like namespaces and cgroups. This design makes containers extremely lightweight and fast to start. You can pack many more containers onto a single host than you could VMs. The trade-off is a less robust security boundary. A vulnerability in the shared kernel could potentially allow a malicious container to escape its sandbox and affect other containers or the host system.
The Performance and Cost Equation
When it comes to performance, containers typically have the edge. Their minimal overhead means faster startup times and more efficient resource utilization. This translates directly to cost savings in cloud environments, as you can run more applications on a single, less expensive machine.
VMs, while more secure, come with a greater performance penalty and higher costs. The resource demands of running a full OS for each instance mean you’re paying for more CPU and memory per application.
Another aspect to take into account (specially those days with a lot of AI running up there), is when you need some GPU, when you need to talk directly to the OS. Using a container, you have a very limited access to the OS, while using VMs, you can build full application based on the running OS.
The traditional advice has always been:
- Use VMs for workloads that require maximum isolation, run legacy applications, direct access to the OS, or need a specific OS not supported by your host.
- Use containers for cloud-native applications, microservices, and rapid, scalable deployments where efficiency is key.
But what if you need both?
The Rise of Secure Container Runtimes
This is where the narrative gets interesting. A number of projects have emerged to give containers the strong security isolation of a VM, without giving up the speed and efficiency we’ve come to love.
Google gVisor
Google’s gVisor is an application kernel that intercepts and handles system calls from the container. Instead of passing these calls directly to the host kernel, gVisor acts as a secure layer, running in userspace. It re-implements a significant portion of the Linux kernel’s API, ensuring a container can’t make a dangerous, unrestricted call to the host OS.
How it works:
- The container believes it’s talking to a real kernel.
- gVisor intercepts these calls and provides a controlled, sandboxed environment.
- This significantly reduces the attack surface compared to a standard container runtime, as a bug in gVisor’s implementation is less likely to lead to a host compromise.
Amazon Firecracker
Firecracker is a lightweight Virtual Machine Monitor (VMM) developed by AWS. It’s designed to create “microVMs” that combine the strong isolation of VMs with the fast startup times and low resource overhead of containers. This technology powers AWS services like Lambda and Fargate.
Key features:
- Minimalist design: Firecracker includes only the essential components for running a guest OS, which drastically reduces its memory footprint and startup time.
- Hardware virtualization: It leverages the Linux Kernel-based Virtual Machine (KVM) to create isolated microVMs, each with its own kernel.
- The result is an incredibly fast, secure, and multi-tenant environment, perfect for serverless functions.
Kata Containers
Kata Containers is another open-source project that uses lightweight VMs to provide enhanced security for containers. It’s designed to be compatible with standard container interfaces like the Open Container Initiative (OCI). This means you can run Kata Containers with existing tools like Docker and Kubernetes.
How it’s different:
- Instead of sharing the host kernel, each Kata Container runs inside a dedicated, lightweight VM.
- It’s a container runtime that plugs into your existing orchestration tools, so you don’t have to change your workflows.
- Kata Containers is a great option when you need to run untrusted workloads on a shared platform, like in a multi-tenant cloud environment, but want to keep the benefits of container tooling.
Practical Takeaways for Developers
So, where does this leave us?
- Standard Containers (like Docker) are still the right choice for most development and production environments. They offer the best balance of speed, efficiency, and tooling.
- Don’t ignore the security risks. The shared kernel model is a real vulnerability. For applications handling sensitive data or running untrusted code, you should seriously consider a more isolated solution.
- For GPU oriented applications, go directly to the virtual machine for optimal performance and resource allocation, ensuring that your workflows are efficiently executed and managed.
- Evaluate secure runtimes for specific use cases. If you’re building a multi-tenant SaaS application or a serverless platform, tools like gVisor, Firecracker, or Kata Containers can provide a critical layer of defense. They are a logical evolution of container technology, giving us the best of both worlds.
The choice between a VM and a container is no longer a rigid either/or. Modern runtimes are giving us the flexibility to select the right level of isolation for each workload, allowing us to build more secure systems without sacrificing performance or developer velocity.



Leave a comment